Production Installation
SkillTree encourages a high-availability and horizontally scalable production installation. To achieve both of these goals, multiple instances of skills-service must be installed on different nodes/instances. Each skills-service node will have the same configuration and is designed to scale-up or scale down horizontally. You can add or remove instances any time.
Tips
Please note that this section is only applicable if you are installing the SkillTree platform from scratch. If your organization is already running a centralized service please proceed to the Integration User Guide or the Dashboard User Guide
There are two installation modes:
- Password Auth Mode: Accounts created and managed by SkillTree and/or delegated to OAuth2 authentication provider (ex. GitHub, Google, etc..)
- PKI Auth Mode: PKI Mode is for intranets where organizations utilize PKI with 2-way SSL certificates to implement authentication and authorization. User's browser must be setup with a personal PKI certificate and that certificate must be issued by a Certificate Authority trusted in the dashboard application's truststore.
Tips
Definitely use Password Auth Mode if you are not sure which mode is applicable to you.
Password Auth Mode Install
Production-grade installation requires a cluster of skills-service daemons which must reside on multiple machines/instances with a load balancer in front of them. There are a number of products that need to be installed in high-availability mode in order to support a clustered SkillTree setup.
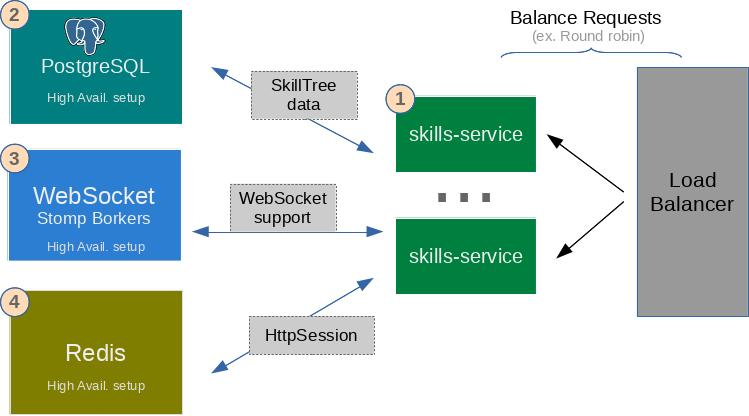
1: Clustered deployment of skills-service for high-availability and higher throughput
- Route requests through a load balancer
2: Database - We currently only support PostgreSQL for a production-grade install
- Make sure to install PostgreSQL in high-availability mode
- PostgreSQL 's installation, setup and management is beyond the scope of this section, please visit https://www.postgresql.org .
3: WebSocket Stomp Brokers
- Some options include Amazon MQ or RabbitMQ
- Make sure to configure high-availability setup
- RabbitMQ 's installation:
- Docker based: RabbitMQ on DockerHub
- Native install: RabbitMQ.com
4: Spring Session for HTTP Session Management: Required for a clustered skills-service deployment to persist HttpSession
- SkillTree uses Spring Session for managing a user’s session information in a clustered environment without being tied to an application container-specific solution.
Tips
SkillTree recommends using JDBC to store the HTTP session in a clustered environment due to its simplicity, and since a shared PostgreSQL instance is already required there is no need to run a separate product. For example, adding the following two properties is all that is required to utilize the existing SkillTree PostgreSQL database for session management:
spring.session.store-type=jdbc
spring.session.jdbc.initialize-schema=always
5: Shared keystore for JSON Web Token (JWT) Generation: Required for a clustered skills-service deployment for JWT generation. If running your SkillTree server in https SSL mode, you can use the same keystore file for JWT by adding the following property:
security.oauth2.jwt.useKeystore=true
Auth Mode skills-service Configuration
Here is a minimum required list of configurations in order to run production-grade skills-service instance(s). Please visit the Configuration section to learn how to configure skills-service.
Each skills-service instance should be configured with the following:
DB configs:
spring.datasource.url=jdbc:postgresql://<server>:5432/skills
spring.datasource.username=
spring.datasource.password=
WebSocket Stomp:
skills.websocket.enableStompBrokerRelay=true
skills.websocket.relayHost=
skills.websocket.relayPort=
Store HttpSession in JDBC:
spring.session.store-type=jdbc
spring.session.jdbc.initialize-schema=always
Keystore for JWT:
security.oauth2.jwt.useKeystore=true
Configure https:
server.port=8443
server.ssl.enabled=true
server.ssl.key-store-type=PKCS12
server.ssl.key-store=/path/to/keystore.p12
server.ssl.key-store-password=
# Force TLSv1.2 until https://bugs.openjdk.java.net/browse/JDK-8241248 is fixed
server.ssl.enabled-protocols=TLSv1.2
Java VM option to increase skills-service heap size:
-Xmx2g -Xms2g
PKI Auth Mode Install
Production-grade installation requires a cluster of skills-service daemons which must reside on multiple machines/instances with a load balancer in front of them. There are a number of products that need to be installed in high-availability mode in order to support a clustered SkillTree setup.
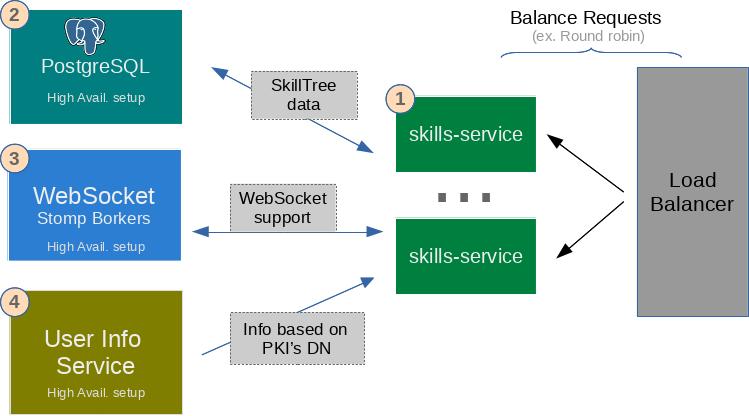
1: Clustered deployment of skills-service for high-availability and higher throughput
- Route requests through a load balancer
2: Database - We currently only support PostgreSQL for a production-grade install
- Make sure to install PostgreSQL in high-availability mode
- PostgreSQL 's installation, setup and management is beyond the scope of this section, please visit https://www.postgresql.org .
3: WebSocket Stomp Brokers
- Some options include Amazon MQ or RabbitMQ
- Make sure to configure high-availability setup
- RabbitMQ 's installation:
- Docker based: RabbitMQ on DockerHub
- Native install: RabbitMQ.com
4: User Info Service - Provides user information based on PKI's Distinguished Name (DN)
- You are responsible for implementing this service, please visit the User Info Service section to learn more.
- Make sure to run it in High Availibility mode
PKI Mode skills-service configuration
Here is a minimum required list of configurations in order to run production-grade skills-service instance(s). Please visit the Configuration section to learn how to configure skills-service.
Each skills-service instance should be configured with the following:
DB configs:
spring.datasource.url=jdbc:postgresql://<server>:5432/skills
spring.datasource.username=
spring.datasource.password=
WebSocket Stomp:
skills.websocket.enableStompBrokerRelay=true
skills.websocket.relayHost=
skills.websocket.relayPort=
Store HttpSession in JDBC:
spring.session.store-type=jdbc
spring.session.jdbc.initialize-schema=always
Keystore for JWT:
security.oauth2.jwt.useKeystore=true
Enable PKI mode install:
skills.authorization.authMode=PKI
Configure https and 2-way SSL:
server.port=8443
server.ssl.enabled=true
server.ssl.client-auth=want
# Force TLSv1.2 until https://bugs.openjdk.java.net/browse/JDK-8241248 is fixed
server.ssl.enabled-protocols=TLSv1.2
# keystore
server.ssl.key-store=/certs/keystore.p12
server.ssl.key-store-password=
server.ssl.keyStoreType=PKCS12
# truststore
server.ssl.trust-store=/certs/truststore.p12
server.ssl.trust-store-password=
server.ssl.trustStoreType=PKCS12
User Info Service client properties:
# To retrieve user info by DN
skills.authorization.userInfoUri=https://<host>:<port>/userInfo?dn={dn}
# Used by dashboard dropdowns to suggest existing users
skills.authorization.userQueryUri=https://<host>:<port>/userQuery?query={query}
# skills-service checks the health of User Info Service
skills.authorization.userInfoHealthCheckUri=https://<host>:<port>/actuator/health
If User Info Service utilizes 2-way SSL then add the following client authentication properties (Java System Properties):
# Keystore
-Djavax.net.ssl.keyStore=/certs/keystore.p12
-Djavax.net.ssl.keyStoreType=PKCS12
-Djavax.net.ssl.keyStorePassword=
# Truststore
-Djavax.net.ssl.trustStore=/certs/truststore.p12
-Djavax.net.ssl.trustStoreType=PKCS12
-Djavax.net.ssl.trustStorePassword=
Java VM option to increase skills-service heap size:
-Xmx2g -Xms2g